The Bottom Line
Small business is important to Central Oregon, and to Mid Oregon. Find tips and resources for business, and information about Mid Oregon’s commercial services and business members.

QR Code Fraud—Are you at risk?
What are QR Codes?
QR codes provide quick access to specific websites or products (for example restaurant menus), but they can also lead to dangerous phishing schemes or infected websites.
Cybercriminals are exploiting the growing use of QR codes as a “touchless experience” during the pandemic. QR interactions have grown 94% over the last three years, with an estimated 5.3 billion QR coupon redemptions projected in 2022. In QR code fraud, the goal is almost always the same—to get you to navigate to a website where cybercriminals can steal your data, money or both. However, there are many ways to protect you from these cybercriminals.
How to Identify Threat:
Tampered QR codes trick consumers by directing them to a malicious site which is designed by the cybercriminal to look identical to the site the victim is attempting to access. Believing the site is authentic, they are then prompted to share confidential information, such as their online banking login credentials or other personal information. Malicious QR codes may also contain embedded malware, allowing criminals to also gain access to the victim’s mobile device and location. Cybercriminals have the ability to tamper with both digital and physical (printed) QR codes on display in public locations.
How to Protect against this Threat:
Consumers can protect themselves by checking that the website the QR code links to is authentic with a correctly spelled and secure URL. Physical QR codes should be highly scrutinized and checked to make sure it was not tampered with by placing a sticker on top of the original QR code, for instance. Also, consumers should be cautious of downloading QR code apps due to the risk of malware. In short, only scan QR codes you are sure are directing you to a trusted site.
Want to know more? Read additional Mid Oregon blog articles about online security and fraud protection.
Content based on an article by Wespay

Remote Education Security Concerns
K-12 Students and Online Learning-Schools, Parents Failing Security
Since the coronavirus pandemic struck, educating children in the U.S. became a challenge to figure out. Online, remote education is still considered the safest way for our children to learn, but it also presents serious online security concerns. Unfortunately, the quick shift to remote education resulted in an outright failure to protect students learning online. Now in the middle of a new school year, how it’s going to work is still being debated. It could include in-person, hybrid (a combination of remote and in-person), and remote education. In our changing environment, there are large remote education security concerns. The time for schools and parents to protect the online security of our students is now.
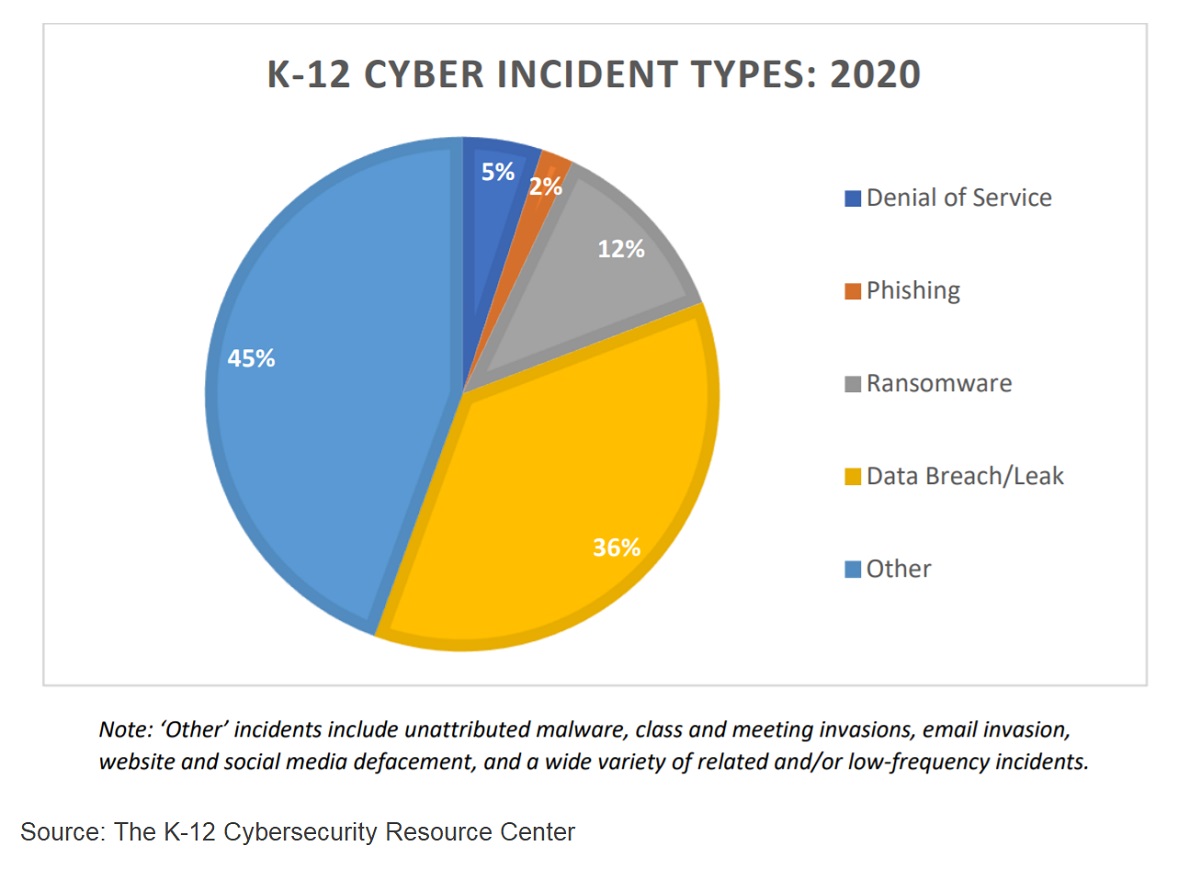
Failing Security Grades
An organization that tracks K-12 cybersecurity incidents, the K-12 Cybersecurity Resource Center, says “The public assumption that K through 12 information security has kept pace with the rest of society is wrong…School districts throughout the United States suffer from notoriously poor information security.” The organization has been tracking cybersecurity incidents with K-12 students since 2016, and to date confirms over 1,100 of these incidents have occurred.
Both schools and parents can improve online security for students with these tips provided by the U.S. Cybersecurity and Infrastructure Agency (CISA) and McAfee security.
Helpful Tips
Share information carefully. Before sharing personal information, consider where it will end up and who may be viewing it. CISA says that’s especially true for video conferencing apps like Zoom and collaboration platforms. Shared screens should have only the information needed visible. Use blurred backgrounds when possible.
Device cameras are a gateway for intruders and security incidents, according to McAfee. Disable chat when possible, and pay close attention to unintended screen sharing, instant messages, and video chats like those from “Zoombombing” incidents.
Don’t hesitate to mute all involved with larger meetings. According to CISA, “ensure you have the capability to mute all attendees and limit the ability of attendees to share screens…consider giving participants an option to participate by audio only if they have privacy concerns…”
Sharing too much information is very risky, says both CISA and McAfee. Don’t put birth dates, location, and phone numbers on learning apps whenever possible. Use a school-provided email address and login info rather than using personal accounts.
Have a vetting process, says CISA. Consider a waiting room to verify participants arriving for a remote learning class before it starts.
Require multi-factor authentication (MFA) for learning apps when possible, says CISA. It’s an easy and effective way to keep hackers out of the online learning process.
Read more “Stickley on Security” on Mid Oregon’s Security and Fraud Center page.
Read more articles on Mid Oregon’s blog about online security

Accessory Dwelling Units—What Are They?
What is an Accessory Dwelling Unit?
An accessory dwelling unit, or ADU, is an old, but simple idea—having a second small dwelling on the same grounds (or attached to) your regular single-family house. ADUs go by several names, including granny flats, in-law suites, accessory houses, or carriage houses.
What qualifies as an Accessory Dwelling Unit?
To qualify as an ADU, the unit must have a fully functional kitchen, full bathroom and living space. It may be attached to a house or garage, or it can also be built as a stand-alone unit. Typically, you won’t be able to access the primary home from inside the ADU. Also, unlike multifamily properties, which have their own separate utilities and addresses, an ADU will usually share the same utilities and address with the primary residence.
What are the benefits?
ADUs can be used in so many different ways and have great potential benefits and positive impacts for owners. Here are a few:
Increased Property Value. A separate living structure can easily raise property value and, if selling, bring more potential buyers to the table.
Housing for Elderly Family Members. The comfort of offering family members their own private space while still being close by and available is reassuring for everyone.
Hosting Family and Guests. Separate accommodations outside the main house give privacy and relaxation to all parties.
Rental Income. An ADU on your property can provide supplemental short- and long-term income.
Home Office Space. Remote work has become more common and having a space free of distractions can be beneficial.
Can I finance an Accessory Dwelling Unit?
If you are looking for ways to finance the building of an ADU on your property, you may be research construction loan options. However, some lenders may not do these type of loans for ADUs and if they do, they may not be the best option for homeowners. More popular financing options include a cash-out refinance, home equity loan, home equity line of credit or a personal loan. Discuss what financing option is best for you with your local credit union.
Whether it’s housing for loved ones or additional income, building an Accessory Dwelling Unit is worth looking into and can bring limitless value to your life.
To learn more about ADUs and home financing options, register for our upcoming free webinar presented by our Mid Oregon Home Loan team on March 17, 10:00 a.m.
Want to know more? Read additional Mid Oregon blog articles about home loans and lines of credit.
