Cybercriminals continue to improve the tools they use for phishing scams. They steal money, identities, credentials, and more every day from individuals and organizations. Even the most cyber-savvy users can be scammed if they don’t pay close attention. To protect yourself, it’s helpful to understand the different types of phishing scams.
Email Phishing Scams
Email is the most popular type of phishing scams. Victims open and act on phishing emails that include fake domain names and redirected URLs. The email’s subject line and content often look legitimate and designed to get a response. Cybercriminals use many tricks to gain your trust, hoping you won’t notice.
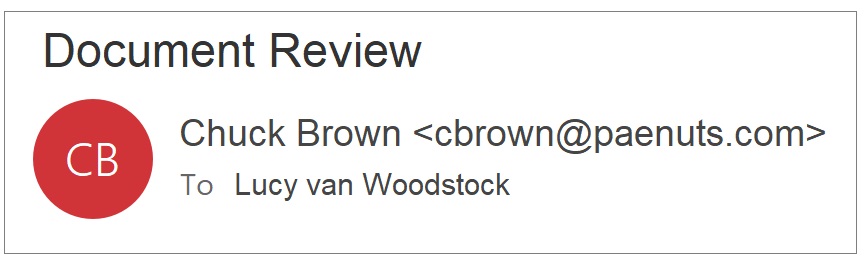
- Closely examine URLs, including spelling. Fraudsters transpose, add, and delete letters to misspell a web address that brings you to a duplicate, fraudulent website. Subtle details like leaving the “s” off of “https” in the URL is another red flag.
- Avoid following links or opening attachments in emails. Instead, type the true URL for the website because links can easily and quickly redirect you to bogus websites and attachments loaded with malware. Be sure to not misspell the domain to avoid Typosquatting attacks detailed below.
- Don’t trust, instead verify email senders, before providing any sensitive information at work and home.
Spear Phishing
Spear phishing is a version of email phishing scams that targets recipients by name, known interests, work relationships, friendships, and other details. With social engineering, scammers scour social media to gather information about targets. Using public information and data from breaches, cybercriminals develop targeted email attacks.
- Limit the information you post on social media, such as Facebook, Instagram, and LinkedIn, and other websites that spear phishers look to exploit.
- Use two-factor authentication (2FA) or multi-factor authentication (MFA) whenever possible. Each layer of verification ensures the right person is accessing accounts and not someone claiming to be you.
- Use artificial intelligence (AI) tools to alert you of compromised accounts.
Whaling
Whaling is a type of spear phishing that targets those at upper levels of management who control of funds. Leaders are not spoof-proof and are vulnerable to the same phishing tricks that target staff. Here are some tips to help ward off whaling.
- Verify Client Certificates are legitimate.
- Set email filters to a level that flags suspicious senders, even before they make it to an inbox.
- Financial transactions should have the highest levels of verification, including face-to-face verification tools.
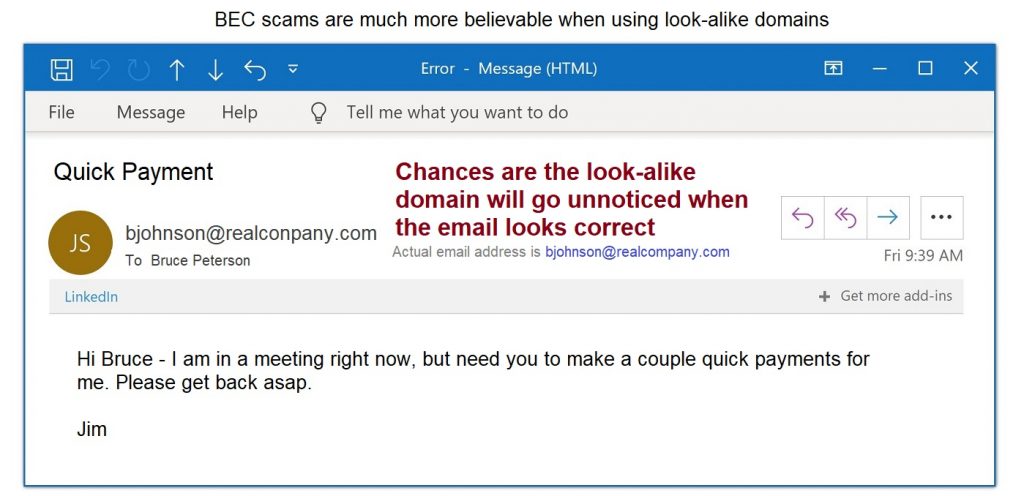
Smishing and Vishing
Smishing uses SMS and text messages for phishing scams. The text message usually has a legitimate-looking link and sometimes includes the first or last few numbers of an account. Victims assume it is legitimate and then take steps that compromise an account and other confidential information.
Vishing attacks are voice calls, many robocalls, that intend to scare recipients into responding with confidential information.
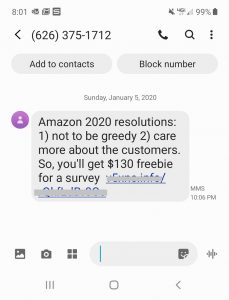
- Never answer a text or phone call from a sender you can’t verify before supplying any information.
- Hang up and redial the phone number directly. Chances are you’re a vishing target.
- Never respond directly to a text message that’s looking for information or includes links.
- Go directly to the true source to verify the sender. Look up the real phone number or website URL and call or browse there. This approach will help determine if it is a legitimate request and whether your information is needed.
Typosquatting
Also called URL or domain hijacking (do-jacking), typosquatting uses incorrect spellings for URLs, or typos a user does without realizing. Minor deviations in spelling can bring you to a look-alike, spoof website. Many of these sites can disappear immediately after stealing your payment card and other information.
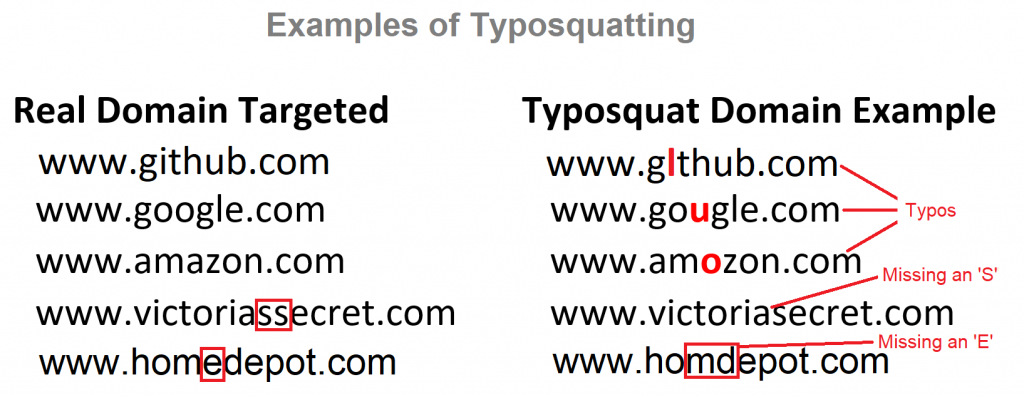
- Check and double-check URL spellings before connecting. Making sure every character, hyphen, and apostrophe is in place.
- Use previously bookmarked sites when possible.
Angler Phishing
One of newest and fastest-growing phishing scams is angler phishing. It uses social media spoof sites to trick users into providing information. These sites often masquerade as social media customer service and ask for sensitive information. They often threaten to close the account or take other action if the data isn’t provided.
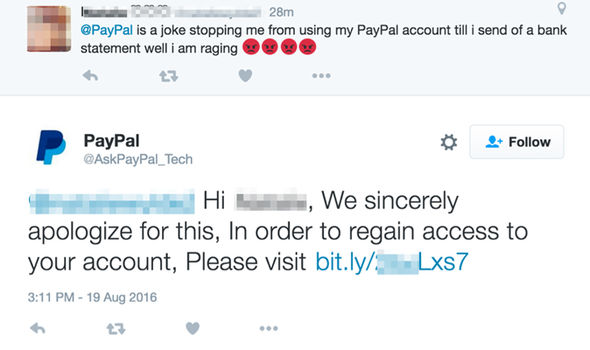
- Address account issues only on the official social media website.
- Look for an official blue checkmark verification symbol, like those found on Twitter and Instagram messaging.
For more articles on phishing scams, cybersecurity and related topics, visit Mid Oregon’s Security and Fraud Center.

