The Bottom Line
Small business is important to Central Oregon, and to Mid Oregon. Find tips and resources for business, and information about Mid Oregon’s commercial services and business members.

Keeping Up
By Chris O’Shea*
Investments that can be inflation-proof
In May, consumer price inflation hit 8.5 percent, the largest yearly increase in more than forty years. It might be time to consider how you’re investing. Here are some moves to make so that your portfolio outpaces inflation.
Treasury Inflation-Protected Securities
As the name suggests, Treasury Inflation-Protected Securities (TIPS) are bonds that are shielded against inflation. With TIPS, the principal increases and decreases with consumer prices. TIPS pay interest bi-annually at a fixed rate that is applied to that adjusted principal. TIPS are issued at five, 10, or 30-year terms. Once they mature, you can either receive the adjusted or original principal. The danger with TIPS is that if inflation doesn’t go that high, your return with typical bonds could be better.
Commodities
Commodities — raw materials like oil, natural gas, wheat and corn — are another good investment tool to protect against inflation. As US News reports, as the price of raw materials goes up, so does the price of consumer goods. That enables you to then get a good return on your commodities investments.
Real Estate
People will always need a place to live, so real estate is a good idea, too. Just like commodities, the value of real estate tends to increase when inflation is high — although to be fair, it has been increasing a great deal over the past few years. That means is that, sure, in the short term your returns might go down, but typically real estate value returns rather quickly as the economy improves.
*This guest article is from the “Your Money Blog” in Mid Oregon’s Digital Banking Credit Savvy resource. It is made possible by SavvyMoney. “Keeping Up” by Chris O’Shea was published in June 2022.
ADDITIONAL INFORMATION
See additional articles by Chris O’Shea in the Mid Oregon View.

Duck Race Kicks off June 29
Yes, it’s time! The Great Drake Park Duck Race kicks off June 29, with ticket sales again being sold in-person as well as online. Mid Oregon Credit Union is again one of the title sponsors under the “Credit Unions Working Together” banner.
Tickets Sold In Person & Online
Tickets for the Duck Race go on sale June 29. This year marks the 33rd consecutive year of local Rotary clubs, businesses and community members raising much-needed funds for local non-profit organizations. The Duck Race has raised nearly $2 million since it began in the late 1980s.
The Duck Race Back On September 11
After a two-year hiatus, the ducks are back and eager to race down the river on September 11, although ticket sales for the Duck Race kicks off June 29. This year we will be selling tickets in person as well as online! Duck race raffle tickets are $5 and can be purchased at First Community, Mid Oregon, OnPoint, and SELCO Credit Union or online at www.theduckrace.com. Local Rotarians and the Duck mascot will also be out in the community promoting ticket sales throughout the summer. Look for them at familiar venues such as Newport Avenue Market.
Twenty prizes with total value over $18,000 will be raffled, including the Grand Prize of $5,000 cash! Additional prizes include a Hoodoo Ski Area season family pass, diamond earrings from Saxon’s Fine Jewelers, and much more.
Fundraiser directly supports local community charities
2022 ticket sale proceeds will benefit the Boys & Girls Clubs of Bend, Central Oregon Veterans Outreach (COVO), Deschutes Children’s Foundation, and MountainStar Family Relief Nursery.
Many Local Organizations Are 2022 Prize Sponsors

The Great Drake Park Duck Race is presented by local Rotary clubs and sponsored by Credit Unions Working Together (First Community, Mid Oregon, OnPoint, and SELCO Credit Union).
2022 prize sponsors include Bend Heating & Sheet Metal, Cascade Insurance Center, Century Insurance, Compass Commercial, Hoodoo Ski Area, Hutch’s Bicycles, Johnson Brothers Appliance, K1 Speed, Les Schwab, Miller Lumber, PacificSource Health Plans, The Pennbrook Company, RBC Wealth Management. Saxon’s Fine Jewelers, Stereo Planet, Webfoot Painting, Zivney Financial Group. Media and other sponsors include Bend Parks and Rec, Bend Radio Group (Mix 100.7, KSJJ 102.9, Power 94, 92.9FM, Backyardbend), The Bulletin, Cascades Business News, Central Oregon Daily, Combined Communications (99.7 The Bull, KBND, 107.7 The Beat, 98.3 The Twins, 101.7), News Channel 21, Smartz, Source Weekly, and Wahoo Films. In-kind support includes Carlson Sign, Sign Pro, and Xpress Printing.

Ignoring Your Credit Report Could Be Costly
As you’re reading this, a cyberthief could be buying a new vehicle with your credit. Hacker’s with access to financial accounts can do significant damage to your credit, quickly and with anonymity. Ignoring your credit report could be costly. To find out if this is happening to you—check your credit report. Checking your report can show any recent purchase activity made with your credit. If you do notice unauthorized activity, acting quickly can make it easier to recover if you ever are a victim.
It’s no secret that hackers are always prepared with email phishing campaigns, malware, ransomware, and various financial and identity fraud attacks. Since the average person is often the prime target of attackers, checking your credit report can show details about your finances you had no idea were happening. A criminal with access to your credit report can open accounts in your name, get loans, credit cards, and make purchases using your stolen identity and passwords. A victim can literally be locked out of their accounts—and no one wants that. Remember, victims are responsible for any and all financial damage done to their accounts. And, it’s not so easy to repair it.
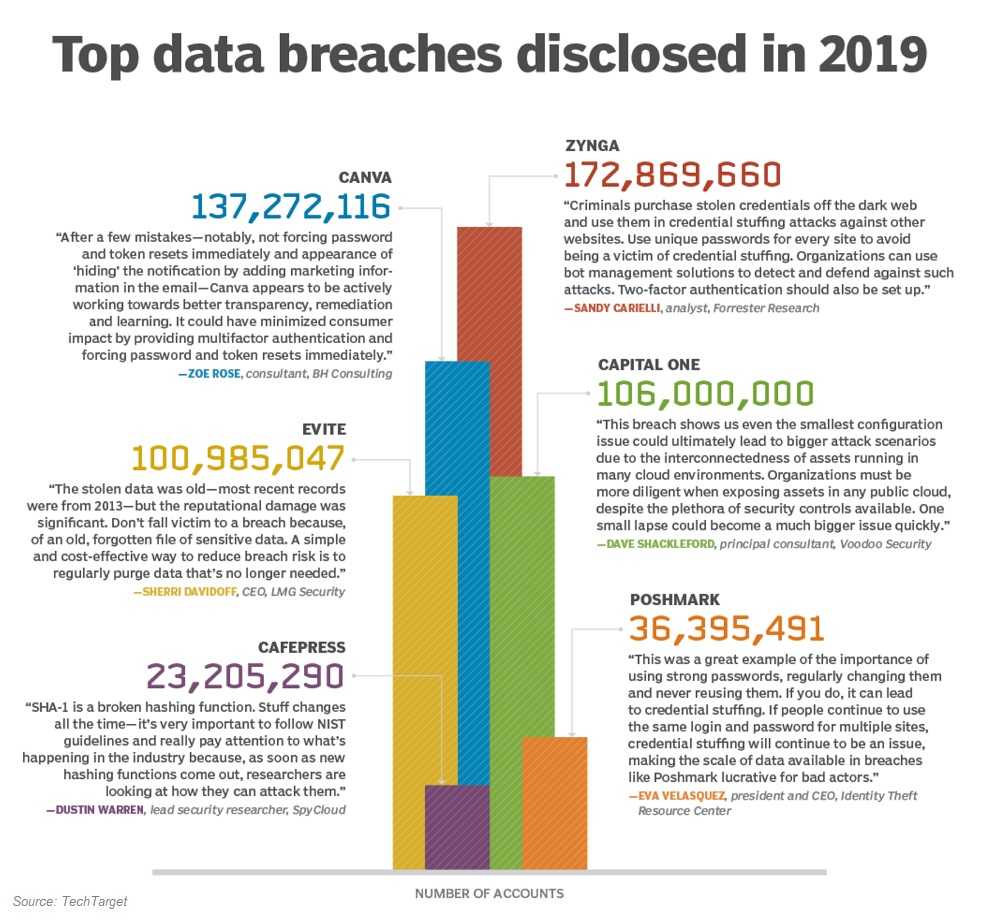
The now infamous 2017 Equifax data breach,—one of the largest identity theft crimes of the decade, is a reminder of just how vulnerable your credit and other data can be. Equifax is one of the top three credit bureaus; the other two being TransUnion and Experian. In the attack, the PII (personally identifiable information) of 148 million Americans was stolen, along with millions more in England and Canada. The hack stole the credit card details, Social Security numbers, dates of birth, driver’s license numbers, and more. The enormity of the attack led to the company agreeing to compensate those affected. But for most victims, it was too little too late. For them, the excruciating process of restoring their identity and credit began.
How To Obtain Your Credit Report
You can get your credit report from several sources including the three major credit reporting agencies (Equifax, TransUnion, Experian). You can also take advantage of Mid Oregon’s free, secure option Credit Savvy located in Digital Banking. When you enroll you will receive access to your credit score, as well as key information from your credit report. You can also sign up for emails to alert you to changes to your credit report.
Mid Oregon has a great resource in helping you protect yourself online. Visit our Stickley on Security resource in our Security and Fraud Center. There, you can read timely articles on a variety of digital security topics, including some videos. Get the most up-to-date information to keep your financial accounts cyber smart.
In the age of increased identity fraud, there’s never been a more crucial time to pay attention to your credit report.
Want to know more? Read additional Mid Oregon blog articles about online security and fraud protection.
Content based on an article by Stickley on Security
