The Bottom Line
Small business is important to Central Oregon, and to Mid Oregon. Find tips and resources for business, and information about Mid Oregon’s commercial services and business members.

What You See Is Not What You Get; Phishing Attack Skips Email Security Measures
Four minute read time.
It’s no surprise that phishing is still prevalent in the cyber world. In fact, it remains the top way malware gets onto devices, and it still excels at getting people to give up their personal information. Phishing scams aim to deceive individuals into sharing sensitive information such as passwords, payment card details, or all other kinds of personal data. Some of this data you wouldn’t even think is all that useful to someone trying to scam you.
The fact is, any piece of information a cybercriminal has about you can be put to use in some sort of scam. That’s why they are so persistent at attempting to get to all the information possible. And as we are staying on top of the attacks better now, they are also getting better at fooling us.
A New Phishing Scam
Most often, we see links in email or in text messages that encourage us to click them. However, in a recent scam, Check Point security is warning about the use of images. It’s quite clever because we typically can spot phishing by finding errors in grammar, graphics, or use of the language. But images are not looked at. In this particular scam, the image may appear to come from a big retailer, such as Amazon or Target, promising special perks.
Here are some valuable tips to avoid falling victim to phishing scams:
Be Vigilant and Verify
Be skeptical of all unsolicited emails, messages, or phone calls asking you to click a link or image or ask for personal information. Legitimate organizations typically do not request sensitive data via email or other insecure channels. Even if they do, back out of the request and log into your accounts to check for these notifications rather than clicking something in a message.
Verify the authenticity of the sender by confirming email addresses, domain names, and website URLs. Cross-reference any suspicious requests or offers by contacting the organization directly using their official contact information. Don’t reply directly to, or click on any links, in one of these messages. The hackers are waiting for you on the other end.
Strengthen Password Security
Create strong, unique passwords for each of your accounts and change them regularly. Enable two-factor authentication (2FA) whenever available, as it adds an extra layer of protection by requiring a secondary verification method, such as a code sent to your phone. However, if you have the option to use a hardware key, an authenticator app, or key fob that generates random codes, choose one of those over email or text codes.
Educate Yourself
Stay informed about the latest phishing techniques and scams. Be cautious of common phishing red flags; such as poor grammar, urgent requests for personal information, or offers that seem too good to be true. These do still exist and aren’t slowing down.
Three well-known phishing scams
There are numerous phishing scams and endless versions of many of them. Following are a few that come around on a regular basis, albeit in various forms.
“Nigerian Prince” or Advance Fee Fraud
This scam typically involves an email from someone claiming to be a wealthy individual or a government representative seeking assistance in transferring funds. The victim is enticed to provide their personal information or financial details in exchange for a promised share of the money.

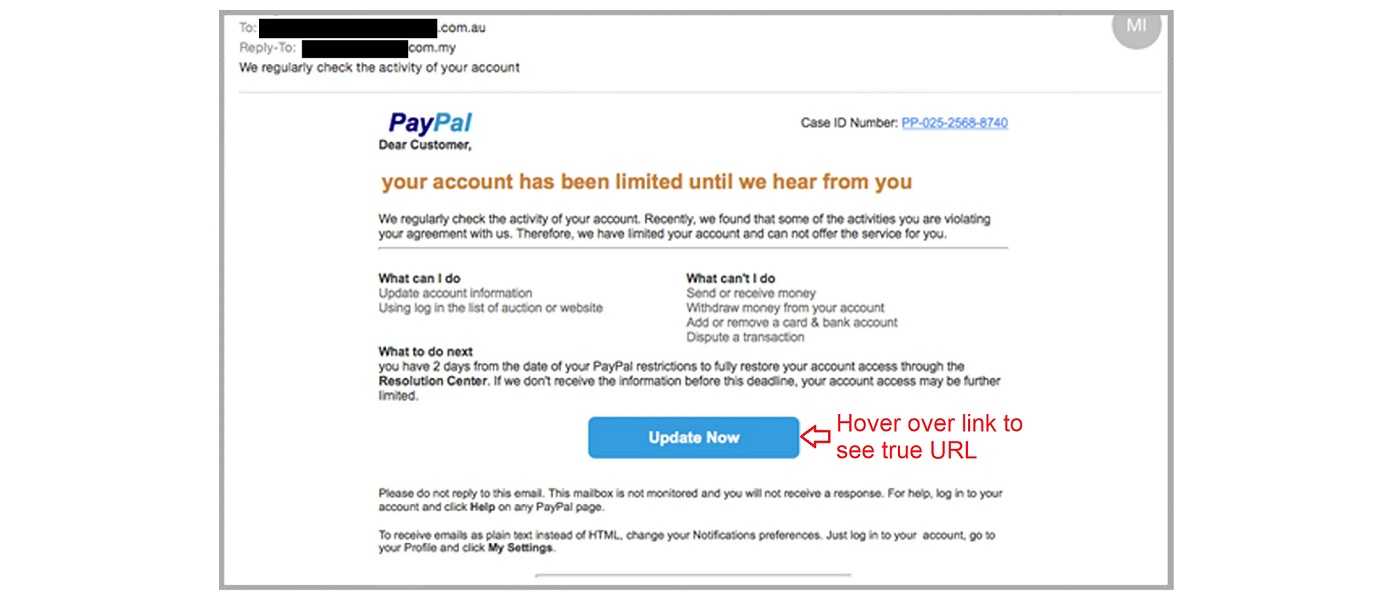
PayPal or Financial Institution Impersonation
Scammers send emails impersonating well-known payment processors or banks, requesting users to update their account information or confirm suspicious transactions. Victims are directed to fraudulent websites that collect their login credentials and sensitive data.
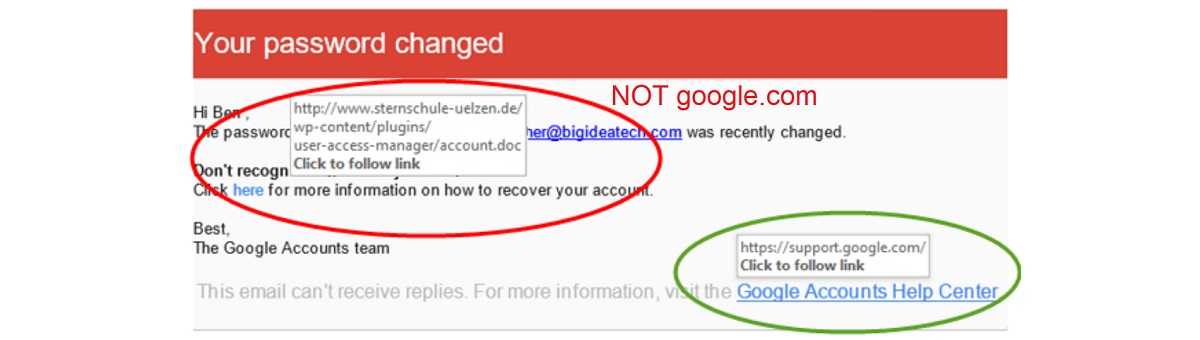
Phishing Emails from Tech Companies
Cybercriminals send emails pretending to be from tech giants like Google or Microsoft, informing users of compromised accounts or the need to verify their information. These emails often contain links to fake login pages designed to harvest login credentials.
Never get in a rush. It’s never so urgent that you can’t take a bit of time to verify if it’s a real request. Actual urgent situations require a phone call to you or 911, not an email message. If it’s really that important, they won’t take time to wait on an email reply. Take the time you need to make sure you’re not getting snagged by a phishing hook.
Mid Oregon provides a valuable resource for enhancing your online security. We invite you to explore our Stickley on Security section within the Security and Fraud Center. This platform offers timely articles covering a range of digital security topics, along with informative videos. Additionally, you can subscribe to receive news and alerts via email, ensuring you stay informed with the latest updates to keep your financial accounts secure in the digital landscape.
Read additional blog articles on cyber security and fraud.
As a reminder, Mid Oregon will never initiate a call asking for personal or account information via phone, text, or email.
Article provided by Stickley on Security

Simplify Your Credit Card Debt: Take Advantage of Mid Oregon’s 0% Balance Transfer Fee
Carrying credit card debt can feel overwhelming. High-interest rates can quickly spiral out of control, making it difficult to get ahead. With a household average of around $10,757 in credit card debt, many consumers could save hundreds of dollars in interest by transferring balances from high- to low-rate cards.
If you’re looking for a way to consolidate your debt and save money, consider a balance transfer to Mid Oregon Credit Union.
Why Choose Mid Oregon?
- Zero-Percent Balance Transfer Fee: Unlike many other financial institutions that charge hefty fees (often 3% or more), Mid Oregon offers balance transfers with absolutely no fee. This means you keep more of your money where it belongs—paying down your debt.
- Competitive Interest Rates: Mid Oregon offers competitive interest rates on our credit cards, helping you save money over the long term.
- Local Expertise: As a trusted member-owned institution, Mid Oregon is committed to helping you achieve your financial goals. Our knowledgeable team can provide personalized guidance and support throughout your debt repayment journey.
How a Balance Transfer Can Help:
- Consolidate High-Interest Debt: Combine multiple high-interest credit cards into one, making it easier to track and pay off your debt.
- Reduce Interest Payments: Lower interest rates mean more of your payment goes towards principal, helping you pay off your debt faster.
- Take Control of Your Finances: A balance transfer can help you regain control of your finances and break the cycle of debt.
Ready to Simplify Your Debt?
Contact Mid Oregon today to learn more about our balance transfer options. Visit our website, or call 541-382-1795 to speak with a friendly and knowledgeable representative.

Improving Your Financial Health 2025
Don’t blink! Another year has come and gone. Now might be the perfect time to review your financial goals with an eye on improving your financial health for 2025. Many of us will set resolutions around our financial lives, such as saving money, reducing debt, improving credit scores, or funding a large purchase. At Mid Oregon you have access to all the tools you need to manage your finances no matter your situation.
Creating a Budget
Having a budget allows you to better control your money. But many feel daunted by the idea of creating a budget for themselves. Writing down your expenses not only helps you to track your spending patterns, it can identify ways for you to avoid unnecessary spending. For most, once you’ve created a budget, you begin to feel more in control of your financial future.
Begin by writing it all down; your daily coffee, subscriptions, utilities, etc… Even those expenses that seem insignificant to you. Identify the necessary expenses, then prioritize the rest. Try applying the following basic percentage rules:
- The 80/20: One of the simpler rules your can use starts with using 80% of your budget for needs and wants, then save the other 20%. Rather than having a variety of categories, you simply divide you expenses and savings into these two buckets.
- The 70/20/10: This rule starts out by allocating 70% of your monthly bills and daily spending, 20% for saving and 10% for debt payments.
- The 50/30/20: This rule divides your income, allocating 50% to needs (housing, transportation, utilities, groceries), 30% toward wants (eating out, streaming services, hobbies or entertainment), and 20% toward savings.
- The 30/30/30/10: This rule is another popular method that breaks your budget down into 30% for housing, 30% for expenses, 30% debt/savings, and 10% for entertainment/fun.
Using the Financial Checkup feature with Mid Oregon’s digital banking takes about 10-15 minutes and gives you a 360-degree view of your spending. You can continue to monitor your spending throughout the year. With the charts and graphs that show you where you are spending money month to month you can track how you are doing with your budget.
Make Savings a Priority
Perhaps 2025 is the time to focus on building your nest egg for emergencies, retirement, or simply peace of mind. Use a savings goal calculator, such as Mid Oregon’s Savings Goals tool in Digital Banking, to see how much you’d have to save each month. If you see a tax refund in your future, use part of that money to give yourself a head start. You’ve heard it before, “pay yourself first”. It may sound cliché but it’s true. Setting aside 20% of your paycheck before you even see it is a great way to begin. In addition to adding automatic transfers to savings, Mid Oregon offers a variety of savings options and strategies to cater to your unique needs:
- Share Certificates—Enjoy higher returns on your investments and keep your money safe and local. We have amazing rates right now so take advantage of our latest special.
- High Yield Savings Accounts—Savings account with a variable dividend rate that increases as the balance increases (minimum balance $1,000).
- IRA Accounts—Build your future and your nest egg faster with attractive rates of return and choices to fit every budget and savings goal.
- Saver’s Club Certificate—Set your goal and the amount you want to save every month. It’s ideal for saving for something special or not being caught short during the holidays.
Work on Minimizing Debt
If reducing debt is on your agenda for the year, Mid Oregon can also assist you in navigating this challenging journey. We offer a variety of loan options designed to help you consolidate your debts and manage them more efficiently. Consider applying for a home equity line of credit (HELOC) to consolidate debt or build an ADU for extra income. How about transferring your high-interest rate credit card balance and take advantage of our no balance transfer fees?
The Most Important Number, Your Credit Score
Improving your credit score is another crucial aspect of financial wellness, and Mid Oregon can help you navigate this process. Many of us don’t keep track of our credit scores, but having a good score influences the type of financial options available to you—including interest rates on loans.
Mid Oregon has a free, secure option that can help you take charge of your credit. Credit Savvy (My Credit Score) on our Digital Banking platform can help you improve your score, and monitor for potential fraud. When you enroll, you receive anytime, anywhere access to your credit score. Plus, you’ll receive simple, straightforward tips that you can use to improve your score. In addition, you’ll enjoy these other features:
- Articles on ways to improve your score.
- Information on how your score compares to other consumers in your area.
- Credit Simulator Tool. Try different what-if scenarios to see how they’ll affect your score—before you make a change!
- Free credit monitoring. Sign up to receive alerts on new accounts or inquiries on your credit report.
- Special offers tailored to your good credit that can reduce your interest rates and save you money!
For those who are interested in building or repairing their credit, we off resources such as secured credit cards and credit builder loans, designed to assist in creating a positive credit profile and boosting your creditworthiness.
Do You Really Need It?!
It’s easy to lose track of how much money you spend on items you do not need. It might be on sale or “fit perfectly on the table corner.” Keep in mind that these unnecessary purchases can affect your bottom line. Get disciplined by identifying your needs vs wants. Do you need the newest smartphone or do you merely want it? Think about giving yourself a 24-hour cooling-off period between the time you see an item and when you make the purchase. If you’re shopping online, consider putting the item in your shopping cart and then walking away until you’ve had more time to think it over. In some cases, you might even get a coupon code when the retailer notices you abandoned the items in your cart. Turning down something you want now may be difficult, but the reward will be greater savings later.
Automating Routine Banking Tasks
- Digital Banking to ease financial tasks, saving you time and increasing your efficiency.
- Automatic overdraft protection. In a few easy steps, you can link your savings account to your checking to have a little added cushion in the event your expenses get a bit tight.
- Automatic loan payments. Your monthly loan payment will automatically be deducted from a linked checking or savings account.
- Setting up auto pay. This is a great way to save you time, hassle and offer peace of mind knowing your bills are paid promptly every month.
- Automate your savings: Direct deposit your paycheck into multiple accounts, including one for each of your savings goals.
As we embark on another new year, it’s essential to remember that achieving your financial goals requires dedication, discipline, and sometimes, a helping hand. Mid Oregon is committed to being that helping hand for you, providing the resources, expertise, and support needed to make positive changes in your financial well-being. So, take advantage of our offerings, and let this year be the one where you turn your financial resolutions into accomplishments.
Regardless of your financial situation, your Mid Oregon team is here to help you every step of the way—please stop by, call, or visit us online at midoregon.com. We also encourage you to stay tuned to future member newsletters, blogs, and workshops for more financial fitness topics.
